Bullseye!
I’ve recently been updating various Debian Buster boxes to Bullseye. I’ve got a couple of laptops to do yet but the rest run Sid.
On my headless servers, the update mainly consisted of - make sure you’re running the latest kernel and latest Buster packages, add the new Bullseye repo’s, update, remove old packages and configs, reboot and then remove the old kernel:
apt update && apt dist-upgrade
cat << "EOF" > /etc/apt/sources.list
deb http://deb.debian.org/debian/ bullseye main
deb http://deb.debian.org/debian/ bullseye-updates main
deb http://deb.debian.org/debian-security/ bullseye-security main
EOF
apt update
apt full-upgrade
apt dist-upgrade
apt --purge autoremove
apt purge $(dpkg -l | awk '/^rc/ { print $2 }')
apt-get clean
reboot
apt purge linux-image-4.19*
I kept all config files like sshd_config. On the desktops the main difference was adding the contrib/non-free repo’s, see also Debian’s instructions.
I’ve also ordered an OrangePi R1+ to use as a router between my new FTTP install and my work laptop. That will run Armbian which I think is still based off Buster, same as most SBC’s including the Vero4K+. The design for that is basically double-NAT, so plug OrangePi WAN interface into Smarthub2 LAN and laptop into OrangePi LAN which does ip masquerading/forwarding and runs a DHCP server and wondershaper for bandwidth management - which is also off by 10x, so to limit to 512kb up/1024kb down you’d call wondershaper enp2s0 5120 10240
Speaking of FTTP:
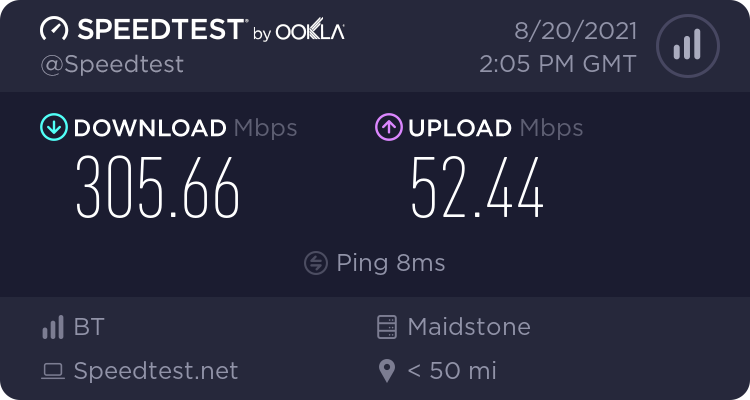
I found that OpenVPN couldn’t actually cope with more than about 50mbps, so I configured IPSEC in a VM, which is a bit buggy shall we say - apart from the fact that some websites don’t even seem to work under IPSEC, charon-nm can’t handle reconnections, my workaround for that was:
cat << "EOF" > /etc/network/if-post-down.d/charon
pkill charon-nm
nmcli device disconnect enp4s0
EOF
It also acts as a killswitch so that when the VPN disconnects, it also downs the ethernet interface (as well as killing charon-nm so it can start again).
Other than that, the process was - install StrongSWAN, OpenVPN and the NetworkManager plugins, disable some useless services and IPv6, and enable the firewall:
cat << "EOF" > /etc/nftables.conf
#!/usr/sbin/nft -f
flush ruleset
add table ip filter
add chain ip filter INPUT { type filter hook input priority 0; policy drop; }
add chain ip filter FORWARD { type filter hook forward priority 0; policy drop; }
add chain ip filter OUTPUT { type filter hook output priority 0; policy accept; }
add rule ip filter INPUT ct state related,established accept
add rule ip filter INPUT ct state invalid drop
add rule ip filter INPUT iifname "lo" accept
add rule ip filter OUTPUT iifname "enp4s0" ip daddr 192.168.1.1 accept
add rule ip filter OUTPUT ip daddr 192.168.1.0/24 drop
add table ip6 filter
add chain ip6 filter INPUT { type filter hook input priority 0; policy drop; }
add chain ip6 filter FORWARD { type filter hook forward priority 0; policy drop; }
add chain ip6 filter OUTPUT { type filter hook output priority 0; policy drop; }
EOF
apt install strongswan-nm strongswan-charon libcharon-extra-plugins strongswan network-manager-openvpn-gnome
systemctl stop avahi-daemon.service
systemctl stop avahi-daemon.socket
systemctl mask avahi-daemon.service
systemctl mask avahi-daemon.socket
systemctl disable --now strongswan-starter.service
systemctl enable --now nftables
sed -i 's/^GRUB_TIMEOUT=.*$/GRUB_TIMEOUT=2/' /etc/default/grub
sed -i 's/^GRUB_CMDLINE_LINUX=.*$/GRUB_CMDLINE_LINUX="ipv6.disable=1"/' /etc/default/grub
update-grub
OpenVPN config and certs can then be imported from the .conf files, IPSEC is more manual, but tends to only require a CA cert plus username/password. I found that IPSEC can definitely exceed 200mbps, buts still not the full 300mbps.